Abstract
This research Project is to develop fingerprint Based Exam Hall Authentication systems that assist in the elimination of examination impersonation. Up till now, the Namibian Universities (particularly IUM) Examination control board is not using fingerprint as mode of identification, this has resulted in people sitting for examinations for others who collect the result at the end. With the adoption of fingerprint biometric, this will be eliminated as fingerprint identification will also be employed during collection of results and certificates. This target can be mainly decomposed into image preprocessing, feature extraction and feature match. For each sub-task, some classical and up-to-date methods in literatures are analysed. Based on the analysis, an integrated solution for fingerprint recognition is developed for demonstration. This demonstration program is coded using C programming language for the program, some optimization at coding level and algorithm level are proposed to improve the performance of this fingerprint recognition system. These performance enhancements are shown by experiments conducted upon a variety of fingerprint images. Also, the experiments illustrate the key issues of fingerprint recognition that are consistent with what the available literatures say. Main objective is to eliminate any form impersonation during exam by employing a more secured means of fingerprint biometrics.
Introduction
Authentication has always been a major challenge in all types of examination. Verification of the authentic candidate is not an easy task, and also it consumes a lot of time and process. This led to the design of Fingerprint based exam hall authentication system that is designed to pass only users verified by their fingerprint scan and block non verified users. Formal examination can rightly be defined as the assessment of a person‘s Performance, when confronted with a series of questions, problems, or tasks set him/her, in order to ascertain the amount of knowledge that he has acquired, the extent to which he is able to utilize it, or the quality and effectiveness of the skills he/she has developed. During the 19th century, formal written examinations became regular in universities, schools, and other educational institutions. Examinations were also increasingly employed for the selection of recruits to the civil service, and the professions, and to posts in industry and commence. Over the ages, standardized testing has been the most common methodology, yet the validity and credibility of the expanded range of contemporary assessment techniques have been called into question. There are two types of systems that help automatically establish the identity of a person: 1) Authentication (verification) systems and 2) Identification systems. In a verification system, a person desired to be identified submits an identity claim to the system, usually via a magnetic stripe card, login name, smart card, etc., and the system either rejects or accepts the submitted claim of identity (Am I who I claim I am?). In an identification system, the system establishes a subject‘s identity (or fails if the subject is not enrolled in the system database) without the subject‘s having to claim an identity (Who am I?). The topic of this paper is channel towards the development of examination impersonation elimination system and this system would strictly do with the unique feature of identification by means of finger print. A verification system based on fingerprints, and the terms verification, authentication, and identification are used in a loose sense and synonymously. Accurate automatic personal identification is becoming more and more important to the operation of our increasingly electronically interconnected information society. Traditional automatic personal identification technologies to verify the identity of a person, which use ―Something that you know, such as a personal identification number (PIN), or ―something that you have, such as an identification (ID) card, key, etc., are no longer considered reliable enough to satisfy the security requirements of electronic transactions or differentiate between an authorized person and an impostor who fraudulently acquires the access privilege of the authorized person. Biometrics is a technology that uniquely identifies a person based on his physiological or behavioral characteristics. It relies on ―something that you are to make personal identification and therefore can inherently differentiate between an authorized person and a fraudulent imposter. 1.1 Background An examination board is an organization that sets examinations and is responsible for marking them and distributing results. Examination boards have the power to award qualification to students. Most exam boards are running as non-profit organizations. IUM is the first and only private owned University in Namibia, which can offer qualification in variety of discipline and well-structured certificates, High certificates, Diplomas, Honours Degrees, Master degrees and Doctorates in different Disciplines such as Telecommunication, Information Technology, Human Resource, Nursing, Education etc. For IUM to be recognised, Respected and set their standard height, it need to establish a secure methods of registration, verification, identification and authentication to make sure that who registered at the beginning of the year is the one who is going to seat to write that exam. 2 The systems that are used currently are not secure because it require a student to provide certain physical documents such as student cards, examination admission slip, etc. This types of methods (documents) can be forged by almost anyone in this fast growing computer technology world. Adoption of Fingerprint Based Exam Hall Authentication system that permit only registered student to enter exam hall and block anyone who wasn’t registered.
Significance of the study
With the increasing rate of exam malpractices in the educational sectors, the Universities management deserve to inculcate a tight security means to ensure that these activities of exam impersonators stops. The activities of these exam impersonators have seen the educational sector suffer some serious form corruption ranging from registered student, to examination supervisor. So it best for the educational body to set up strategies and some certain security means to stop this aspect of corruption in the educational sector. The system uses a finger prints biometrics, this will help ensure that only registered student during registration with their finger prints are allowed into the examination hall. The system would 3 contribute in the area of stopping any activity of corruption in the educational sector among students, and student to teachers. Hard work would be encouraged as every registered student knows he/she is going to write the exam by him or herself. The impersonation which has been eating the educational system there by encouraging laziness among students would be eliminated and standard of student educational performance would be increased.
Technical
This system was implemented using Protease and C Programming Language: Embedded C and also all necessary method of data collection reachable to ensure the system meet up to acceptable standard has been put into consideration. Also this work would be carried out under close supervision of Engineer Nkrumah for adequate guidance and interpretation of the work as it unfolds. During the design of this system, the most of effort is on simulation lather than fabrication, fabrication part of the system will come in place during implementation phase once everything in place and running to avoid wasting of resources, because most of the equipment used in here were bought and are very sensitive if handled otherwise.
Fingerprint Module
This is a fingerprint sensor module with TTL UART interface for direct connections to microcontroller UART or to PC through MAX232 / USB-Serial adapter. Which can store the finger print data in the module and can be configured in 1:1 or 1: N mode for identifying the person. The FP module can directly interface with 3v3 or 5v Microcontroller. A level converter (like MAX232) is required for interfacing with PC serial port. Optical fingerprint imaging involves capturing a digital image of the print using visible light. This type of sensor is, in essence, a specialized digital camera. The top layer of the sensor, where the finger is placed, is known as the touch surface. Beneath this layer is a light-emitting phosphor layer which illuminates the surface of the finger. The light reflected from the finger passes through the phosphor layer to an array of solid state pixels (a charge-coupled device) which captures a visual 6 image of the fingerprint. A scratched or dirty touch surface can cause a bad image of the fingerprint. A disadvantage of this type of sensor is the fact that the imaging capabilities are affected by the quality of skin on the finger. For instance, a dirty or marked finger is difficult to image properly. Also, it is possible for an individual to erode the outer layer of skin on the fingertips to the point where the fingerprint is no longer visible. It can also be easily fooled by an image of a fingerprint if not coupled with a "live finger" detector. However, unlike capacitive sensors, this sensor technology is not susceptible to electrostatic discharge damage. Optical biometric fingerprint reader with great features and can be embedded into a variety of end products, such as: access control, attendance, safety deposit box, car door locks.
Microcontroller (ATmega328)
The Atmel 8-bit AVR RISC-based microcontroller combines 32 KB ISP flash memory with readwhile-write capabilities, 1 KB EEPROM, 2 KB SRAM, 23 general purpose I/O lines, 32 general purpose working registers, three flexible timer/counters with compare modes, internal and external interrupts, serial programmable USART, a byte-oriented 2-wire serial interface, SPI serial port, 6- channel 10-bit A/D converter (8-channels in TQFP and QFN/MLF packages), programmable watchdog timer with internal oscillator, and five software selectable power saving modes. The device operates between 1.8-5.5 volts. The device achieves throughputs approaching 1 MIPS per MHz The choise of this type of microcontroller is influenced by the number of ports and internal memory that the component poses, enough ports to connect all of the components of the project and the enough memory for buffering and store fingerprints scan samples for simulation purposes..
MC Programming Language: Embedded C This is the most widely used programming language for embedded processors/controllers. Assembly is also used but mainly to implement those portions of the code where very high timing accuracy, code size efficiency, etc. are prime requirements. Embedded C is perhaps the most popular languages among Embedded Programmers for programming Embedded Systems. There are many popular programming languages like Assembly, BASIC, C++ etc. that are often used for developing Embedded Systems but Embedded C remains popular due to its efficiency, less development time and portability.
Protease 8.0
The Proteus Design Suite is a proprietary software tool suite used primarily for electronic design automation. The software is used mainly by electronic design engineers and technicians to create schematics and electronic prints for manufacturing boards. It was developed in Yorkshire, England by Lab center Electronics Ltd and is available in English, French, Spanish and Chinese languages. Schematic capture in the Proteus Design Suite is used for both the simulation of designs and as the design phase of a PCB layout project. It is therefore a core component and is included with all product configuration. Use Proteus software with its strong function in the simulation and analysis to simulate the microcontroller and its peripheral equipment. Design, debug and modify hardware and software of the microcontroller system on the computer. Draw the physical circuit after the successful circuit simulation. It forms a new system design model is: schematic design - simulation circuit design and modification - physical production and testing. The model makes the flaws exposed early in the design, shorts design cycles and reduces experimental costs. While also maximizing student's learning initiative and innovation. It is of great significance in developing innovative and practical talent, reforming the traditional teaching model and improving the quality of experimental teaching.
Methodology
A research methodology is a systematically programming approach of a well-defined procedure that should be followed in caring out a thorough research work. An adequately suitable methodology would ensure a very detail research work and ensure a higher degree of accuracy and efficiency is adopted. In other to attain quiet a reasonable acceptance of the research work, the internationally accepted software engineering model was used, which is During authentication, the biometrics of the user is captured again and the extracted features are compared (using a matching algorithm) with the ones already existing in the database to determine a match. It has been established that physical achieves are not always helpful a much better alternative is to use biometrics concept that can facilitate stronger security to the problem of exam impersonation. This implies the creation of database management system (DBMS) which ensure that computer records are kept up to date and made available on demand to those who need them for planning and operational purpose. The level of success achieved in caring out this research work is owed to the methodology adopted.
Results
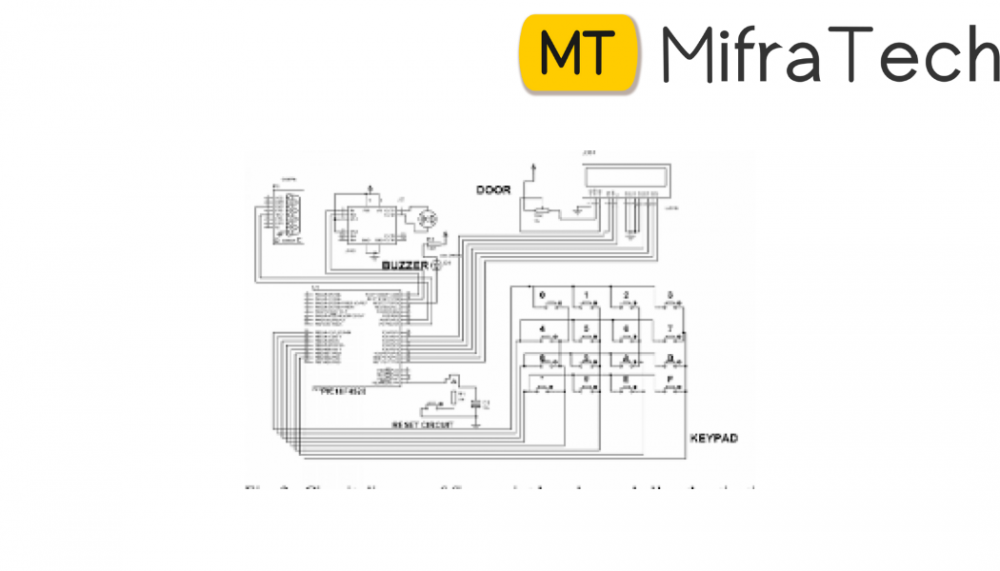
By using this project the design and implementation of ID authentication system based on Fingerprint Identification is designed, and finally, the problem at hand, which is exam student impersonation and corruption is Tertial Education will be demolished and to demonstrate that anything can be achieved using computer technology in this fast growing Information Technology and computer communication world . Simulation phase of this project has been achieved, with the following devices: Microcontroller (Atmega 328), LCD display device (LM016L), regulated DC power supply, Keypad-phone, Virtual Terminal, X1 Crystal clocking, Variable Resistor, and Capacitors. Regulated DC power supply is used for powering the devices on the system and it has to be regulated to avoid too much power to burn the device and to be too low for it to be insufficient for the devices operations. Microcontroller, this is the heart of the whole system, it is there to facilitate the connection between devices, control the operation of every device connected on this system, it has clocking equipment that must be synchronised with the crystal clocking device to ensure precise operation of the system. Keypad, this device is used as a input device used by the user (student) when they are entering their password during authentication process. LCD display is used as the output device of the whole system because, every message that the system need to convey to the user, is display on here, starting from displaying the name of the system (Fingerprint based exam hall authentication), asking the user to place their fingers (Put your finger), displaying the results of the authentication (Enter the passkey or Access denied student not registered) and the final display if the user’s passkey is correct (Access granted). Variable resistor, this is to give brightness to the LCD display. Crystal Clocking, this has the simple task, which is to provide clocking to the system, clocking which is synchronised with the clock of the microcontroller. Virtual Terminal is used as input device as well to input the student number of the student when the system ask the user to put their finger, because there is no fingerprint scanner on the system, so this device is used in the simulation phase. And the final device are the capacitors, which are used to prevent the unwanted current from entering the system.
Conclusion
In this paper a Biometric Model for Examination impersonation and Biometric Access is a better substitute for the use of Identity card in verifying users ‘identity Experience has shown the porosity of Identity cards in uniquely identifying individual in the face of sophisticated Forgery technology. The naturalness in the use of fingerprint makes it a reliable access control technique. The fact that a user no longer needs to carry identity cards and other documents for identification explain the ease of use. The Exam hall authentication system using fingerprints. The implemented minutiae extraction is much more accurate and faster than our previous feature-extraction. In our proposed system accurately verify the fingerprint is valid user or not. If valid user then it allow attending the exam else not allowed. In this experimental result shows the proposed method is suitable for all the authentication based application and also it robust.
embeeded and electronics projects
embedded electronics projects
embedded systems final year projects
embedded based final year projects
embedded related projects
embedded project
embedded projects for ece
embedded system projects for ece
embedded systems mini projects for ece
embedded based projects for ece
embedded systems projects for eee
embedded project ideas
embedded systems final year project ideas
embedded system based final year projects
embedded project topics
embedded final year projects for ece
best ai projects for beginners
https://www.mifratech.com/public/
https://www.facebook.com/mifratech.lab
https://www.instagram.com/mifratech/
https://twitter.com/mifratech