Abstract
Computer security depends largely on passwords to authenticate human users from attackers. The most common computer authentication method is to use alphanumerical usernames and passwords. However, this method has been shown to have significant drawbacks. For example, users tend to pick passwords that can be easily guessed. On the other hand, if a password is hard to guess, then it is often hard to remember. To address this problem, some researchers have developed authentication methods that use pictures as passwords. In this paper, we conduct a comprehensive survey of the existing graphical password techniques and provide a possible theory of our own.
Introduction
Human factors are often considered the weakest link in a computer security system. If we point out that there are three major areas where human-computer interaction is important: authentication, security operations, and developing secure systems. Here we focus on the authentication problem. User authentication is a fundamental component in most computer security contexts. Studies showed that since user can only remember a limited number of passwords, they tend to write them down or will use the same passwords for different accounts. To address the problems with traditional username-password authentication, alternative authentication methods, such as biometrics, have been used. In this paper, however, we will focus on another alternative: using image as passwords. 2. Graphical Password Graphical passwords refer to using pictures (also drawings) as passwords. In theory, graphical passwords are easier to remember, since humans remember pictures better than words [1]. Also, they should be more resistant to brute- force attacks, since the search space is practically infinite. In general, graphical passwords techniques are classified into two main categories: recognition-based and recallbased graphical techniques [2]. 2.1 Recognition Based System In recognition-based techniques, a user is authenticated by challenging him/her to identify one or more images he or she chooses during the registration stage. Recognitionbased systems, also known as cognometric systems [4] or searchmetric systems [3], generally require that users memorize a portfolio of images during password creation, and then to log in, must recognize their images from among decoys. Humans have exceptional ability to recognize images previously seen, even those viewed very briefly . From a security perspective, such systems are not suitable replacements for text password schemes, as they have password spaces comparable in cardinality to only 4 or 5 digit PINs (assuming a set of images whose cardinality remains reasonable, with respect to usability). Recognition based systems have been proposed using various types of images, most notably: faces, random art, everyday objects, and icons. Renaud [3] discusses specific security and usability considerations, and offers usability design guidelines focusing on recognition-based systems. In some graphical password schemes, the system must retain knowledge of some details of the shared secret, user specific profile data e.g. in recognition schemes, the system must know which images belong to a user’s portfolio in order to display them. This information must be stored such that its original form is available to the system (possibly under reversible encryption), and thus may be available to anyone gaining access to the stored information.
Recall Based System
In recall-based techniques, a user is asked to reproduce something that he or she created or selected earlier during the registration stage. Recall-based graphical password systems are occasionally referred to as drawmetric systems [4] because users recall and reproduce a secret drawing. In these systems, users typically draw their password either on a blank canvas or on a grid (which may arguably act as a mild memory cue). Recall is a difficult memory task [5] because retrieval is done without memory prompts or cues. Users sometimes devise ways of using the interface as a cue even though it is not intended as such, transforming the task into one of cued-recall, although one where the same cue is available to all users and to attackers. Text passwords can also be categorized as using recall memory. With text passwords, there is evidence that users often include the name of the system as part of their passwords [6], [7]. Although there is currently no evidence of this happening with graphical passwords, it remains a plausible coping strategy if users can devise a way of relating a recall based graphical password to a corresponding account name.
Proposed System
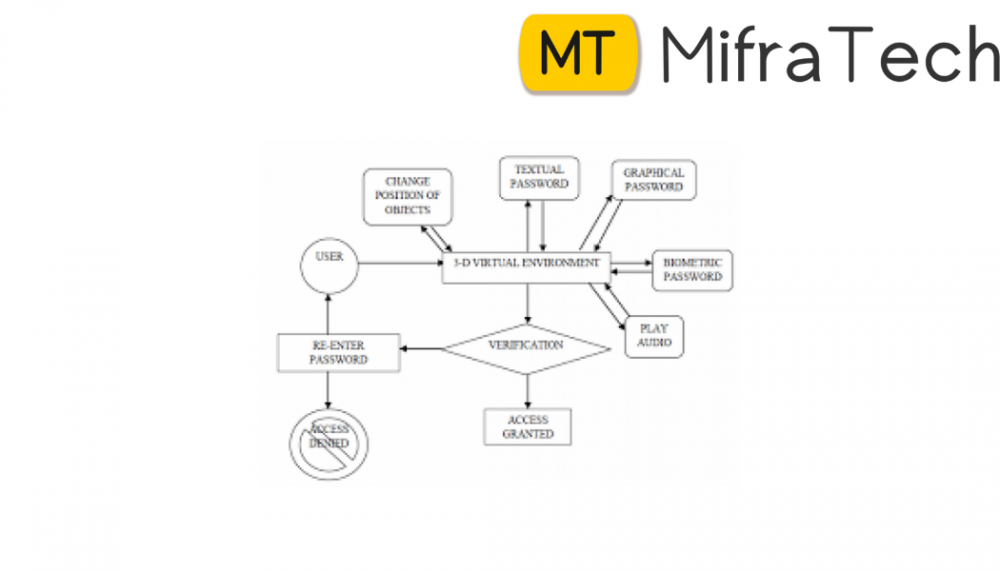
In graphical authentication there are various techniques to secure your password. Here we are proposing a new algorithm of authentication using images. We used a grid based approach to authenticate by using image as a reference. At the time of registration, user will upload his/her image or set of images along with all details; then user selected image will appear on the page with Shoulder surfing is a major drawback of graphical password authentication. To overcome this we have developed SSR (Shoulder Surfing Resistant) shield. The shield containing multiple fake mouse pointers are programed in such a way that it moves randomly in an image area and the original pointer will look exactly as fake mouse pointers. This shield provides a top layer for grid clicking as well as confusing other person. transparent grid layer on it. So user will select certain grids to set his/her password as shown in the figure below.
Implementation and Discussion
The proposed system was implemented using PHP, CSS, JavaScript and Macromedia flash 2008(Action Script 2). This Graphical Password can be implemented in authenticating several systems and websites.
The implementation has few focuses:
• Login: Contains username, images, Graphical password and related methods.
• Grids: Contains unique grid values and grid clicking related methods.
• Password: Contain image as reference & encryption algorithm.
• SSR shield: Containsshield for Shoulder surfing. As shown in the figure below researchers are trying to stabilize the goal in text based system. However, the text based approach is not able to achieve the goal because as the password strength increases usability decreases. Our main aim is to achieve this goal. In which the usability as well as the security of the system is maintained in such a way that we don’t need to compromise on either of these constraints.
Conclusions
In this extended abstract we are trying to make our authentication system more user friendly and also we have tried to implement mature & fast Shoulder Surfing Resistant Mechanism. We have considered both methods: text based and graphical based systems and tried to reduce the efforts required by end-user to remember passwords. A look at the advancement in technology over the past few years tells us that the next era will have system security at its core. Thus Graphical Password may be adapted in future as a major authentication system.
best cse engineering final year projects
best cse projects for final year
best cse projects
best btech projects for cse
best cse project ideas
best computer science final year projects
best projects for cse engineering students
best engineering projects for cse
best cse final year projects
best project for cse students